Xmlrpc.php is a core file in WordPress that facilitates remote communication between your WordPress site and external applications. This file enables remote publishing, mobile app connectivity, and third-party tools that interact with your site. Initially, Xmlrpc.php was crucial for enabling these functionalities, especially before introducing the WordPress REST API.
Understanding Xmlrpc.php is essential for WordPress site owners and developers because it directly impacts site security and functionality. While it provides valuable features, Xmlrpc.php has also been associated with various security vulnerabilities, including brute force attacks and DDoS attacks. Knowing how to manage and secure Xmlrpc.php can help protect your site while maintaining the necessary functionality.
What Is Xmlrpc.php?
Xmlrpc.php is a PHP file included in WordPress that allows data to be transmitted between your website and external systems using the XML-RPC protocol. XML-RPC stands for “XML Remote Procedure Call,” a protocol that uses XML to encode its calls and HTTP as a transport mechanism.
Essentially, this file acts as a bridge, enabling remote applications to interact with your WordPress site by executing predefined functions like publishing posts, editing content, and managing comments.
Within the WordPress architecture, Xmlrpc.php is pivotal in facilitating remote communication. Before the introduction of the REST API, Xmlrpc.php was the primary means for enabling remote management of WordPress sites.
It allowed mobile apps, external blogging clients, and other third-party tools to connect and perform operations on your site without needing direct access to the WordPress admin interface.
While newer methods like the REST API have emerged, Xmlrpc.php is still present in WordPress for compatibility and legacy support, making it an integral part of the platform’s infrastructure.
History and Purpose of Xmlrpc.php
Xmlrpc.php has its roots in the early days of WordPress when the need for remote communication between a website and external applications first emerged. Dave Winer and Microsoft initially developed the XML-RPC protocol in 1998 to facilitate cross-platform communication using a standardized format.
WordPress adopted Xmlrpc.php to allow users to remotely manage their sites, particularly for publishing posts via external blogging clients, integrating with mobile applications, and enabling trackbacks and pingbacks.
In the early 2000s, the ability to manage content remotely was a significant advancement, providing users with the flexibility to interact with their WordPress sites from various devices and applications. Xmlrpc.php became a critical component of WordPress’s infrastructure, supporting the growing need for remote access and automated interactions with the platform.
This functionality was precious before the widespread adoption of smartphones and the creation of dedicated mobile apps, making Xmlrpc.php an essential tool for users and developers alike.
Common Uses of Xmlrpc.php in WordPress
Common uses of xmlrpc.php in WordPress are discussed below.
Remote Publishing
One of the primary uses of Xmlrpc.php in WordPress is enabling remote publishing. This feature allows users to create, edit, and publish content on their WordPress sites from external applications without logging into the WordPress dashboard.
Blogging clients, desktop editors, and other content management tools can communicate with the site through Xmlrpc.php, providing a seamless way to manage content remotely. This capability was precious in the early days of blogging when users relied on third-party editors to draft and publish posts.
Integration with Mobile Apps
Xmlrpc.php plays a crucial role in integrating WordPress with mobile applications. Before introducing the REST API, Xmlrpc.php was the primary mobile app protocol for interacting with WordPress sites.
Through Xmlrpc.php, users could perform various tasks directly from their mobile devices, such as publishing posts, moderating comments, and managing media files. This integration provided the flexibility to manage a WordPress site on the go, making it easier for users to stay connected with their content from anywhere.
Pingback and Trackback Features
Xmlrpc.php is also responsible for handling pingbacks and trackbacks in WordPress. These features allow sites to communicate with each other when linking to content, notifying the linked site that it has been referenced.
Pingbacks are automatic, while trackbacks are manually initiated, but both use Xmlrpc.php to send and receive notifications between WordPress sites. This inter-site communication enhances content visibility and creates connections between related content across the web.
However, it also introduces potential security risks, as malicious actors can exploit these features to spam or launch DDoS attacks.
Security Risks and Vulnerabilities
While Xmlrpc.php provides valuable functionalities, it also introduces several security risks that can compromise a WordPress site. Because Xmlrpc.php allows external applications to interact with a WordPress site, it becomes a potential target for malicious activities.
Over the years, attackers have exploited this file to gain unauthorized access, perform brute force attacks, and launch Distributed Denial of Service (DDoS) attacks, among other security threats. Understanding these vulnerabilities is crucial for safeguarding your site.
Brute Force Attacks
One of the most common security risks of Xmlrpc.php is its susceptibility to brute-force attacks. Since Xmlrpc.php supports multiple authentication attempts in a single request, hackers can use it to try thousands of username and password combinations quickly.
This makes it easier for attackers to gain unauthorized access to a WordPress site by guessing the correct credentials. Once inside, they can take control of the site, inject malicious code, or steal sensitive information.
Distributed Denial of Service (DDoS) Attacks
Xmlrpc.php can also be exploited for Distributed Denial of Service (DDoS) attacks. Using the pingback feature, attackers can send multiple requests to Xmlrpc.php, causing the server to become overwhelmed and ultimately crash.
This attack can lead to significant downtime, disrupting the site’s availability and impacting user experience. Additionally, since Xmlrpc.php can target other sites, your WordPress site could inadvertently become part of a giant botnet to launch DDoS attacks on other websites.
Broader Implications for Site Security
The security risks associated with Xmlrpc.php extend beyond brute force and DDoS attacks. If left unchecked, vulnerabilities in Xmlrpc.php can lead to unauthorized access, data breaches, and the introduction of malware into your WordPress site. Additionally, attackers may exploit Xmlrpc.php to create backdoors or manipulate site settings, compromising the site’s integrity.
Given these broader implications, it’s essential to carefully manage Xmlrpc.php by disabling it or implementing robust security measures to mitigate potential threats.
Why You Should Disable Xmlrpc.php?
Keeping Xmlrpc.php enabled on your WordPress site offers certain benefits, mainly if you rely on remote publishing, mobile app integration, or use plugins and tools that require XML-RPC for communication.
It allows for greater flexibility in managing your site, especially when you need to perform tasks from external applications. Additionally, for users who depend on legacy systems or older blogging clients, Xmlrpc.php remains a critical component.
However, these benefits come with significant security risks. Xmlrpc.php is a known target for hackers, often exploited to perform brute force attacks, DDoS attacks, and other malicious activities.
While enabling Xmlrpc.php can be convenient, it exposes your site to vulnerabilities that could lead to unauthorized access or disruptions. The risks often outweigh the benefits, especially if you refrain from actively using the features that Xmlrpc.php supports.
Disabling Xmlrpc.php is recommended in several scenarios, mainly when security is a priority, and its functionality is not essential. Some critical scenarios include:
- You Don’t Use Remote Publishing or Mobile Apps: If you manage your WordPress site directly through the admin dashboard and don’t rely on external apps or tools that require XML-RPC, disabling Xmlrpc.php is prudent to reduce security risks.
- Concern Over Security Vulnerabilities: If you’re worried about potential security threats like brute force attacks or DDoS attacks, disabling Xmlrpc.php can significantly reduce the attack surface of your WordPress site, making it harder for attackers to exploit these vulnerabilities.
- Limited or No Use of Pingbacks and Trackbacks: If you don’t use pingbacks or trackbacks, or if you’ve already disabled them to avoid spam or DDoS risks, there’s little reason to keep Xmlrpc.php enabled.
- Using Modern Alternatives: If your site relies on the WordPress REST API or other modern methods for remote communication, Xmlrpc.php is no longer necessary. Disabling it can streamline your site’s architecture and improve security.
In most cases, disabling Xmlrpc.php enhances the security of your WordPress site without sacrificing essential functionality, mainly if you rely on newer technologies and methods for site management.
How to Check if Xmlrpc.php is Enabled?
To determine whether Xmlrpc.php is enabled on your WordPress site, you can use several straightforward methods:
- Direct URL Check: The most straightforward way to check if Xmlrpc.php is enabled is by navigating to yourdomain.com/xmlrpc.php in your browser. If the file is enabled, you should see a response such as “XML-RPC server accepts POST requests only.” If disabled, you may receive a 403 Forbidden error, 404 Not Found error, or a blank page.
- Using Developer Tools: You can also use browser developer tools to check if Xmlrpc.php is being loaded. By inspecting network requests while interacting with your site, you can see if Xmlrpc.php is being called. If it is, the file is likely enabled.
- WordPress Admin Dashboard: Some WordPress configurations or security plugins may provide information about Xmlrpc.php directly in the admin dashboard. Look for settings related to XML-RPC under security or site settings.
There are several tools and plugins available that can help you determine whether Xmlrpc.php is enabled:
- XML-RPC Validator: Online tools like the XML-RPC Validator can check if Xmlrpc.php is enabled. Simply enter your site’s URL, and the tool will attempt to connect using XML-RPC and display whether the connection was successful.
- WordPress Security Plugins: Security plugins like Wordfence, iThemes Security, and Sucuri often include features to monitor the status of Xmlrpc.php. These plugins can detect if Xmlrpc.php is enabled and, in some cases, provide options to disable or protect it.
- Pingback Checker: Tools designed to check the status of pingbacks can also help determine if Xmlrpc.php is active. Since pingbacks rely on XML-RPC, if enabled, xmlrpc.php is likely also.
Using these methods and tools, you can easily verify the status of Xmlrpc.php on your WordPress site, helping you make informed decisions about keeping it enabled or disabling it for enhanced security.
How to Disable Xmlrpc.php in WordPress?
There are two ways to disable xmlrpc.php in WordPress: using plugins or tools or manually.
Disabling Xmlrpc.php with Plugins
Several WordPress plugins can help you easily disable Xmlrpc.php without manually editing files. Here are some recommended options:
- Wordfence Security: A popular security plugin that provides comprehensive security features, including disabling Xmlrpc.php.
- iThemes Security: Another robust security plugin that allows you to disable Xmlrpc.php and offers various other security enhancements.
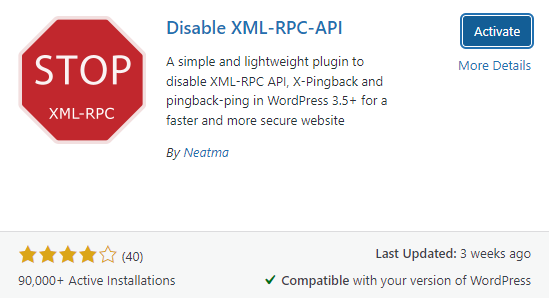
- Disable XML-RPC-API: A specialized plugin explicitly designed to disable Xmlrpc.php functionality related to pingbacks and trackbacks.
Choose a plugin of your choice and follow these steps:
Step 1: Install and Activate the Plugin
- Access Your WordPress Admin Dashboard:
- Log in to your WordPress admin dashboard.
- Navigate to the Plugins Section:
- Go to Plugins > Add New.
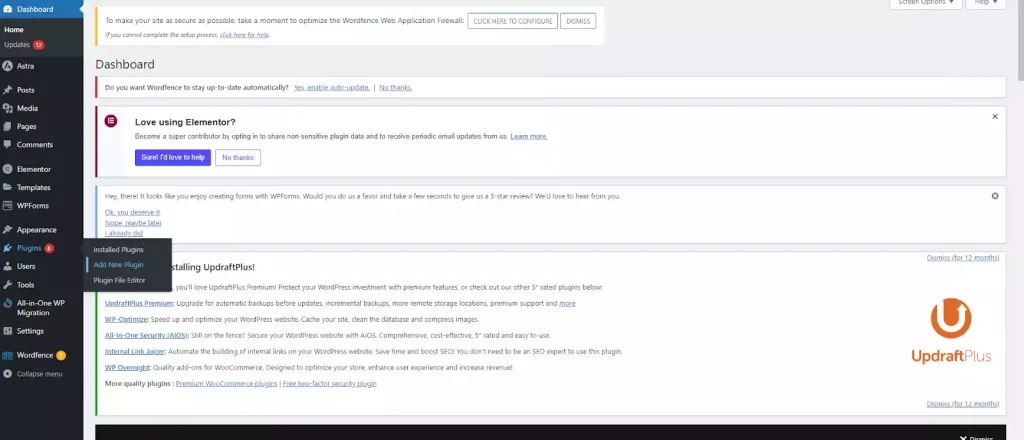
- Search for the Plugin:
- In the search bar, type Disable XML-RPC-API.
- Locate the plugin in the search results, then click Install Now.
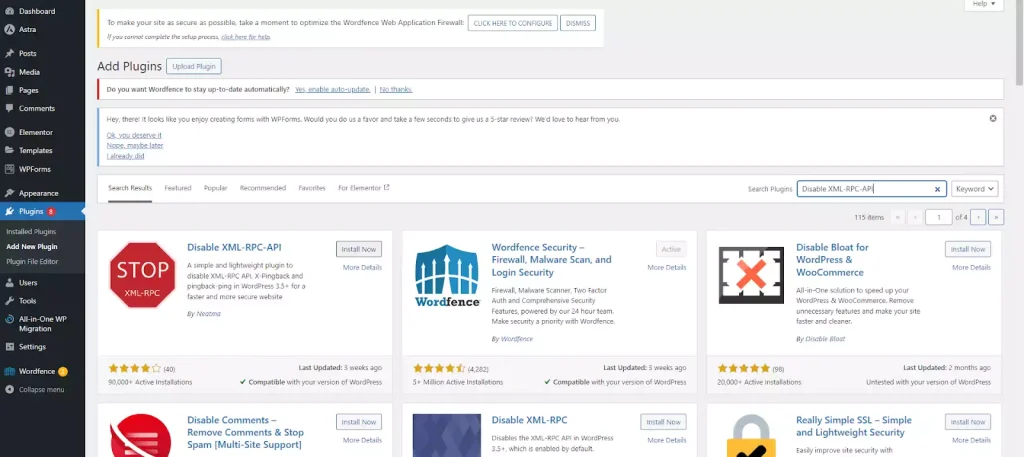
- Activate the Plugin:
- Once the plugin is installed, click Activate to enable it on your site.
Step 2: Plugin Configuration
- Automatic Configuration:
- The Disable XML-RPC-API plugin is designed to work automatically after activation. It disables the XML-RPC and related functionality without requiring any further configuration.
Step 3: Verify and Monitor
- Verify Xmlrpc.php Status:
- After activating the plugin, you can verify that the XML-RPC has been disabled. Use tools or methods mentioned in the guide to check your site’s XML-RPC status.
- Monitor Your Site:
- Please monitor your site to ensure it continues functioning as expected without any issues related to the XML-RPC feature.
By following these steps, you can effectively disable the Xmlrpc.php functionality using the Disable XML-RPC-API plugin, helping to secure your WordPress site against related vulnerabilities.
Disabling Xmlrpc.php Manually
Disabling via .htaccess File
- Access .htaccess File:
- Locate the .htaccess file in your WordPress root directory using an FTP client or your hosting provider’s file manager.
- Edit .htaccess File:
- Open the .htaccess file in a text editor.
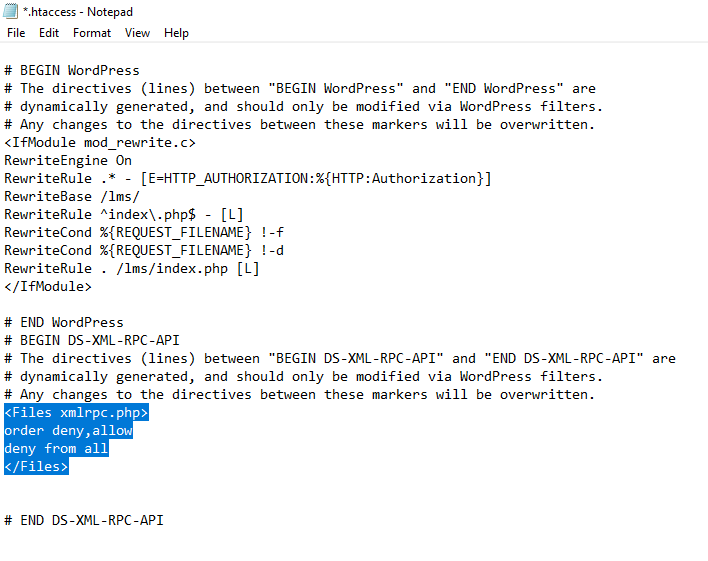
Add the following code to deny access to Xmlrpc.php:
<Files xmlrpc.php>
Order Allow,Deny
Deny from all
</Files>
- Save and Upload:
- Save the file and upload it back to your server. This code will block all users’ access to Xmlrpc.php.
Disabling through Site-Specific Code in functions.php
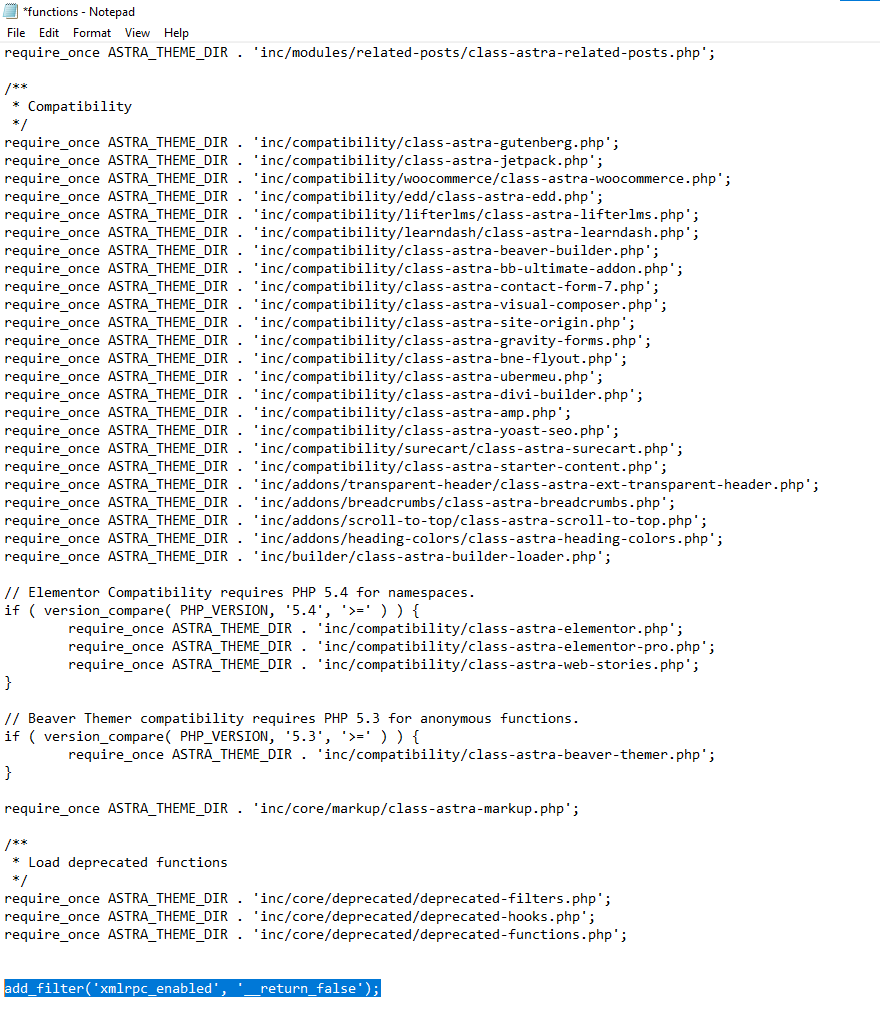
- Access functions.php:
- Navigate to your theme’s functions.php file using an FTP client or file manager. The file is in the /wp-content/themes/your-theme/ directory.
- Add Code to functions.php:
Open functions.php and add the following code snippet:
add_filter(‘xmlrpc_enabled’, ‘__return_false’);
- Save Changes:
- Save the file and upload it back to your server. This code will disable Xmlrpc.php for your site.
Using FTP or cPanel for Manual Disablement
- Access Your Site via FTP or cPanel:
- Connect to your site using an FTP client or your hosting provider’s cPanel file manager.
- Locate Xmlrpc.php File:
- Navigate to the root directory of your WordPress installation.
- Rename or Delete Xmlrpc.php:
- You can either rename xmlrpc.php to something like xmlrpc-disabled.php or delete the file. Renaming is a safer option, allowing you to restore it if needed.
- Confirm Changes:
- Visit yourdomain.com/xmlrpc.php in your browser to check your site to ensure Xmlrpc.php is no longer accessible. If it is correctly disabled, you should receive a 404 error or similar message.
Using these methods, you can effectively disable Xmlrpc.php on your WordPress site to mitigate security risks while maintaining control over its functionality.
Alternatives to Xmlrpc.php
Here are some of the best alternatives to xmlrpc.php
REST API as a Modern Alternative
The REST API is a modern and versatile alternative to Xmlrpc.php for interacting with WordPress. Introduced in WordPress 4.4, it provides a more robust and flexible remote communication and integration method.
- Benefits of the REST API:
- Enhanced Security: The REST API has more advanced security features than Xmlrpc.php, including more granular permission controls.
- Better Performance: The REST API supports JSON format, which is lighter and more efficient than the XML format used by Xmlrpc.php.
- Improved Flexibility: It offers extensive functionality for interacting with WordPress, including retrieving and updating data and creating custom endpoints for specific needs.
- Wider Adoption: The REST API is widely supported and used in modern web and mobile applications, providing better integration capabilities with current technologies.
Other Potential Solutions
Aside from the REST API, other potential solutions can be used depending on your specific needs:
- GraphQL API: An alternative to the REST API, GraphQL provides a more flexible query language for interacting with your WordPress site. It allows clients to request the data they need and nothing more, improving efficiency and reducing data transfer overhead.
- Custom Endpoints and Webhooks: For specialized needs, you can create custom endpoints or webhooks to handle specific interactions with your WordPress site. This approach allows you to tailor communication methods to your requirements without relying on Xmlrpc.php.
- Third-Party Integration Plugins: Several plugins integrate with various third-party services and applications without requiring Xmlrpc.php. These plugins often utilize modern APIs and provide a user-friendly way to connect your site with external tools.
By transitioning to these modern alternatives, you can enhance your WordPress site’s functionality, security, and performance while minimizing the risks associated with Xmlrpc.php.
When You Need to Re-enable Xmlrpc.php?
While disabling Xmlrpc.php can improve security, there are specific situations where re-enabling it might be necessary or beneficial:
- Using Legacy Blogging Clients: If you rely on older blogging clients or external tools that require XML-RPC for remote publishing or management, you may need to re-enable Xmlrpc.php to maintain compatibility.
- Mobile App Integration: Some mobile applications and third-party tools that manage content or provide additional functionalities might depend on Xmlrpc.php. If these tools are crucial for your workflow, re-enabling Xmlrpc.php could be necessary.
- Pingback and Trackback Features: If your site relies on pingbacks and trackbacks for inter-site communication and you prefer to use these features, Xmlrpc.php must be enabled.
How to Safely Re-enable Xmlrpc.php if Needed?
If you decide that Xmlrpc.php is necessary for your site’s operations, follow these steps to re-enable it safely:
- Review Security Measures:
- Before re-enabling Xmlrpc.php, ensure your site has other security measures, such as strong passwords, plugins, and up-to-date software to mitigate potential risks.
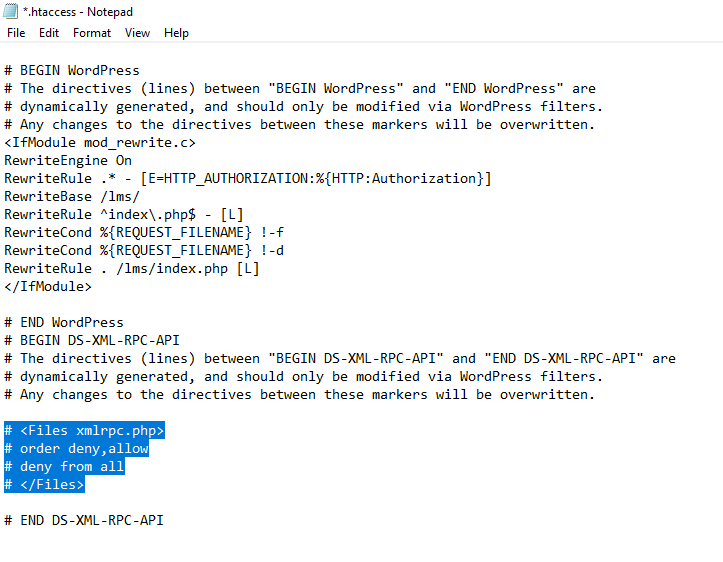
- Enable Xmlrpc.php in .htaccess:
If you had previously disabled Xmlrpc.php via the .htaccess file, remove or comment out the lines that restricted access. For example, delete or comment out the following code:
<Files xmlrpc.php>
Order Allow,Deny
Deny from all
</Files>
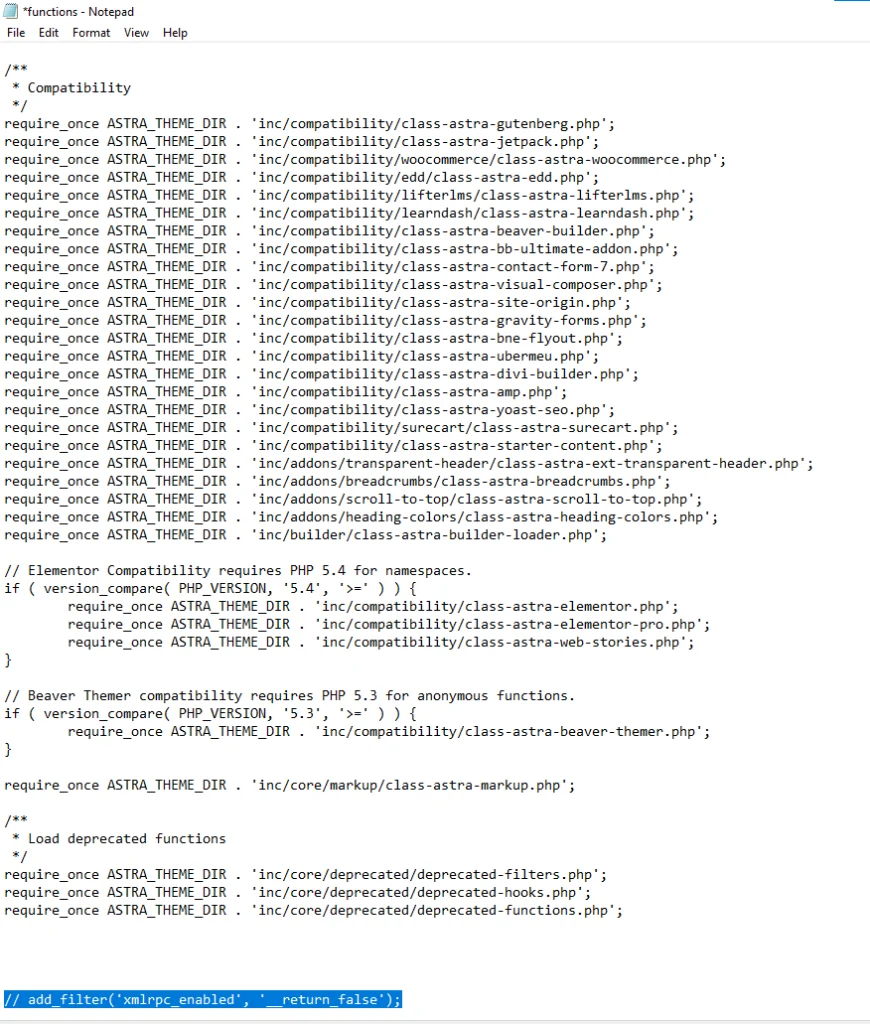
- Re-enable via Functions.php (if applicable):
If you disabled Xmlrpc.php through code in functions.php, remove or comment out the code snippet:
add_filter(‘xmlrpc_enabled’, ‘__return_false’);
- Restore Xmlrpc.php File (if deleted or renamed):
- If you renamed or deleted the xmlrpc.php file, restore it from a backup or download a fresh copy from the WordPress installation package. Upload the file to the root directory of your WordPress installation.
- Verify Functionality:
- After re-enabling Xmlrpc.php, verify that it’s functioning correctly by testing remote publishing, mobile app integration, or any other features that depend on it. Check for any security vulnerabilities or unexpected behavior.
- Monitor for Security Issues:
- Continuously monitor your site for any security issues related to Xmlrpc.php. Check logs, use security plugins, and stay informed about potential threats.
By carefully considering these steps and ensuring that Xmlrpc.php is re-enabled securely, you can balance the need for functionality with maintaining a secure WordPress environment.
Conclusion
Xmlrpc.php is an integral part of WordPress that facilitates remote communication and integration with external applications. Historically, it enabled features such as remote publishing, mobile app connectivity, and pingbacks/trackbacks. However, it also introduces security risks, including susceptibility to brute force and Distributed Denial of Service (DDoS) attacks.
Understanding Xmlrpc.php’s role, associated security concerns, and available alternatives, such as the REST API and GraphQL, is crucial for maintaining a secure and functional WordPress site. Disabling Xmlrpc.php can significantly enhance site security if its features are not essential.
On the other hand, there are situations where re-enabling it may be necessary for compatibility with legacy tools or specific functionalities.
Managing Xmlrpc.php requires a balanced approach that considers benefits and potential risks. For sites where Xmlrpc.php is essential, implementing robust security measures and monitoring its usage is crucial to mitigating vulnerabilities. For sites where its functionality is not required, disabling it can help protect against common threats.
Regularly reviewing your site’s security posture and staying informed about the latest best practices will ensure you maintain a secure and efficient WordPress environment. By understanding how Xmlrpc.php fits into your site’s architecture and carefully managing its use, you can effectively safeguard your site while leveraging the necessary functionalities.